2026 TikTok Shop Growth Guide: How to Boost Sales with AI and GMV Max?
In 2026, TikTok has become an indispensable core player in the cross-border e-commerce market. On one hand, TikTok …
Table of Contents
In the realm of cross-border e-commerce, advertising networks, and international social media marketing, TikTok automation is a crucial step to enhance efficiency and expand scaling models.
However, with the rise of TikTok trends, these methods are exposing systemic risks, with an increasing number of teams encountering limitations, anomalies, and even account bans during the automation process.
The core operation mechanism of TikTok accounts is mainly simulated user actions on the platform, through software simulation interactions like clicking, dragging, tapping, commenting, and liking, to achieve automated management and interactions with account content. Operators often perform in a virtual environment, such as simulators or cloud-based virtual machines, thus enabling simultaneous actions on multiple accounts. To maintain operational efficiency, they will follow pre-set scripts and rules to execute tasks, such as setting time intervals for posting content or limiting the number of comments based on user engagement.
However, this operational mode has limitations: actions generated by the virtual machine are often clustered, repetitive, and usually lack real user behavioral traits and environmental variables (like IP, GPS, language, and time zone real matching), making them easily flagged by TikTok’s identification system as abnormal behavior.
In the cross-border e-commerce and international social media marketing, once a device is banned, it not only directly affects account security and operational continuity but also reflects the increased time, manpower, and capital investment, thus impacting overall sales performance and project ROI.
Under the backdrop of TikTok’s high-risk environment, various alternative solutions and technical pathways are available to ensure performance optimization without affecting the underlying stability. Understanding the principles and limitations of these solutions can aid in crafting a more robust automation strategy.
In this context, closer to real device environment scenarios, techniques based entirely on actual ARM architecture become a focus.
RPA stands for Robotic Process Automation, which is a technology that allows software-based robots to automate repetitive tasks on various devices. The primary objective is to reduce human labor, improve operational efficiency, and optimize workflows.
RPA typically has the following features:
In the context of cross-border operations, RPA is often used for performing high-speed, standardized tasks, such as account logins, content releases, account management, data collection, status monitoring, and more.
Cloud phones are not emulators; they are based on real ARM architecture’s standalone mobile device environments. Their core advantages include:
RPA is mainly responsible for performing repetitive and standardized workflows, such as content releases, engagement activities, and monitoring daily tasks, while cloud phones provide a real, isolated operational environment, allowing these operations to be completed on secure, reliable devices.
In this model, automated actions of each account will operate independently in its cloud phone, avoiding multiple accounts collecting on the same environment and generating risks. The cloud phone itself minimizes the system, storage, and device identifiers, enabling accounts to operate more closely with actual users and deeply reduce the risks of identification by the platform.
By leveraging RPA’s operational management capabilities, operational teams can quickly adapt to novel environments, and configurations can easily evolve, significantly increasing operational efficiency simultaneously while avoiding being flagged as abnormal by the platforms. This means that even managing a large number of accounts concurrently can maintain operational stability and security.
DuoPlus Cloud Phones are specialized for cross-border social media, advertising networks, and e-commerce operations, primarily focusing on providing a safe, standalone, and highly realistic device environment for automated tasks. By combining cloud phones with RPA, teams can ensure account safety firsthand, achieve a standardized and centralized management of operations, and improve operational efficiency and standardized capability.
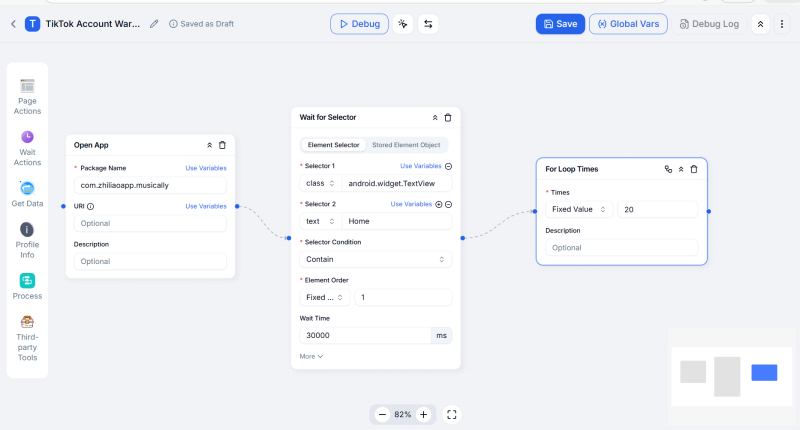
Create Workflows: Users can select to create their custom workflow scripts, starting with setting comprehensive variables, inputting the required data, then adjusting the automated operations via left-side operational controls, and subsequently experiment for device initiation to run tasks, check whether the experimental data flow matches the requirements, and finally deploy as a scheduled task or circular task.
Alternatively, you can use templates from services offering official templates to support TikTok automation, TikTok account management, Reddit account management, etc., allowing for one-click activates for immediate execution of scheduled/circular tasks.
Processing Management: You can check the current state of processed tasks in the processing management module, pause specific task points when paused by task clicks, and execute the first time task immediately.
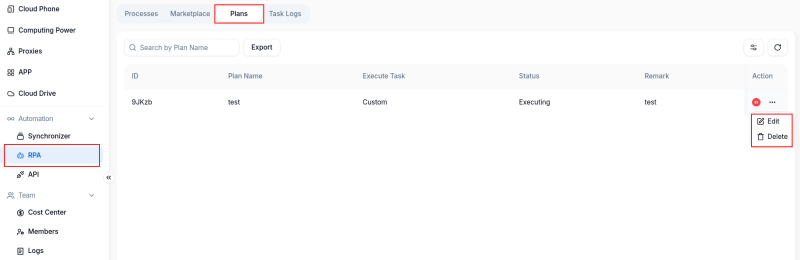
Task Logs: In the task logs module, you can view the operation results of planned tasks, ensuring scheduled tasks are directly saved in the list, waiting until the specified time arrives to continue execution, and you can manually stop during this period if required.
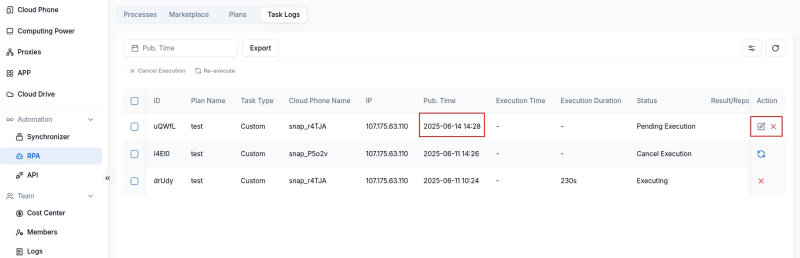
In today’s environment of TikTok automation, a secure and stable operational environment has become a fundamental requirement for each content creator and cross-border operator. The cloud phone integrated with RPA fundamentally provides a controllable, isolated operational space that makes automation processes more realistic and secure, allowing TikTok to leverage ongoing output sustainably.
DuoPlus Cloud Phone
Protect your multiple accounts from being

In 2026, TikTok has become an indispensable core player in the cross-border e-commerce market. On one hand, TikTok …

As a well-known fast-fashion platform, SHEIN has attracted a significant volume of sellers through its vast supply chain …
No need to purchase multiple real phones.
With DuoPlus, one person can operate numerous cloud phones and social media accounts from a single computer, driving traffic and boosting sales for you.
